CrowdStrike’s passive arrogance after disrupting vast swaths of global travel
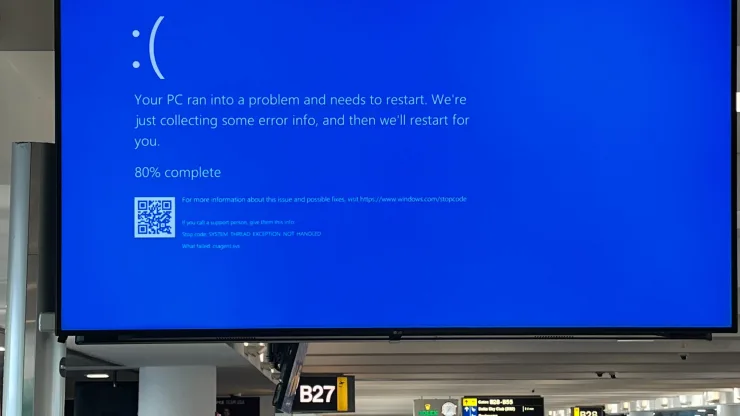
Virtually everything travel-related stopped working this morning, including all flights on United, American, and Delta Air Lines. A cybersecurity researcher called it “The largest IT outage in history.” The outage also crippled hospitals and emergency services.
CrowdStrike, a cybersecurity company’s whose products are used by many large companies, was apparently to blame. It sent out a faulty update that crashed many Windows computers running critical systems. Then it posted a sad, passive, and arrogant little announcement about what happened.
So what did CrowdStrike have to say for itself?
Here’s the statement from CrowdStrike this morning:
Statement on Falcon Content Update for Windows Hosts
CrowdStrike is actively working with customers impacted by a defect found in a single content update for Windows hosts. Mac and Linux hosts are not impacted. This is not a security incident or cyberattack.
The issue has been identified, isolated and a fix has been deployed. We refer customers to the support portal for the latest updates and will continue to provide complete and continuous updates on our website.
We further recommend organizations ensure they’re communicating with CrowdStrike representatives through official channels.
Our team is fully mobilized to ensure the security and stability of CrowdStrike customers.
Update 9:22am ET, July 19, 2024:
We are working hard to provide comprehensive and continuous updates with our global customers as quickly as possible. Below is the latest CrowdStrike Tech Alert with more information about the issue and workaround steps organizations can take. We will keep this page updated with new information as it’s available. [This is followed by a set of technical instructions.]
Passive evasion
This response is very clear. It is also woefully inadequate and passive.
CrowdStrike’s error disrupted a huge collection of machines operating much of the global economy. Fixing it requires rebooting individual machines in safe mode and deleting a file, a clumsy workaround that will slow all recovery efforts to a crawl.
Look at all the passive voice sentences and phrases in its brief statement. Each one is an evasion.
[C]ustomers impacted by a defect [Who caused it?]
Mac and Linux hosts are not impacted. [By whom?]
The issue has been identified, isolated and a fix has been deployed. [By whom?]
Our team is fully mobilized [who mobilized it?]
Here are three reasons why passive voice is particularly egregious here:
- It fails to take responsibility. There is no “we” as in “Our employee sent out a faulty update that caused the problem and we apologize for the disruption.”
- It’s confusing. In a passive voice phrase or sentence, you can’t tell who is acting. It would be good to know what CrowdStrike did, who was in charge, and who is doing what now. Instead, nameless individuals or entities sent out the faulty update, identified the problem, deployed the fix, and mobilized the team. In passive voice sentences the actor is not the subject, so we don’t have a clear idea of what happened or what is going to happen next.
- It’s infuriating. Each passive voice sentence contributes to the reader’s “What the hell is going on?” reaction. Imagine that you are, say, in charge of IT at Delta Air Lines. Your life is a chaotic living hell right now. The same applies to thousands of other businesses and services with millions of customers. Those customers are now cursing their providers, but the true cause of the problem is hiding in the background and saying little more than, “Hey, stuff happens.”
This is arrogant and unforgivable
Causing an outage like this is terrible. But it’s a mistake. It’s a mistake that should never have been made, but it’s still just a human error.
But failing to take responsibility and hiding behind a passive statement is arrogant.
An early, appropriately sincere apology would have created a path for recovery for this company and its executives. Such a statement is way easier than running a cybersecurity company. But it’s clearly beyond the capabilities of CrowdStrike.
Just act like human beings. It’s not all that hard. Pathetic.
Who needs to worry about cyberattacks when your cybersecurity partner can screw things up on a global scale for everyone?
Here’s Claude’s simple removal of the passive voice:
CrowdStrike actively works with customers a defect in a single content update for Windows hosts has impacted. Mac and Linux hosts remain unaffected. This situation does not constitute a security incident or cyberattack.
We have identified and isolated the issue and deployed a fix. We refer customers to the support portal for the latest updates and will continue to provide complete and continuous updates on our website.
We further recommend organizations ensure they communicate with CrowdStrike representatives through official channels. Our team has fully mobilized to ensure the security and stability of CrowdStrike customers.
I don’t love it, but at least it’s less weaselly.
Claude is unable to fix the problem because the actors in these sentences are unknown. “We” is only marginally better. As usual the humans at CrowdStrike, not a generic AI, must fix the problem.
Ugh Claude’s version might be worse, anyone who uses an AI tool to write something about a global IT outage they caused has totally lost the plot. Save AI generated text for emails you don’t care about. Read it again, it’s jargony without an element of real humanity in it. It is a really bad idea to encourage people to use this kind of text. Though – if you want to run a simulation on it just to remove passive language as a teaching moment then fine…
The reason is simple. Legal liability. To admit fault would open themselves up to massive lawsuits, as guilt would have already been admitted. Suing them would be easy money for anybody, as victory in court would be assured by their admission of guilt. This is why insurance companies always advise people in car crashes to never admit fault.
Passive, smassive.
In the middle of a catastrophic situation like this, who gives a #)%> about passive voice?
CEOs and other executives of the airlines, hospitals, 911 operations and other major organizations affected by Crowdstrike’s screwup? Nope. They probably won’t even read the releases. They just want assurance from Crowdstrike’s top people that Crowdstrike understands the problem, has a fix in hand, and is working their butts off to get their systems up and running as soon as possible. Oh, and they’ll also want assurances that something like this will never happen again.
Crowdstrike’s attorney’s? Yes, as Josh Lehan explained so well above.
Employees of Crowdstrikes customers, who are all “assholes and elbows” trying to “stanch the bleeding?” Nope. They’re too busy.
The flying public, hospital patients, and other ordinary folks affected by Crowdstrike’s screwup? Nope. They just wanna put this behind them and get on with their lives as quickly as possible.
I’d bet most everyone who read Crowdstrike’s releases was able to understand quite clearly what happened, what was happening, and what was planned to happen. And I don’t think they much cared about identifying specifically who or what was responsible for which part of the situation – at least while the fires were still burning.
There are times and places to criticize passive voice and other aspects of BS writing. This was not one of them.
In a related aside, I’m astonished by two facets of this situation.
1. Given the number of systems that were to receive this update I’m amazed that Crowdstrike apparently didn’t test their update on a large enough number of their own systems to detect the problem before they distributed it to their customers.
2. I’m even more surprised that Crowdstrike’s customers themselves apparently didn’t install the update on internal test systems to try to detect any problems before going live with it.
I’ve been retired from the IT world – DEC and Compaq – for more than 20 years. We and our customers always made sure the software updates we released had been tested on many representative systems before they went live. Sure, we had occasional problems but never because of something as simple as a bad file. Shame!
Tom
Thanks for your comment.
In fact, at this moment, the attitude conveyed by the CrowdStrike folks is essential. The future of their company and of our trust in the IT system depends on what they do now. And they’ve blown it by communicating that this is just a technical problem and failing to acknowledge the harm they’ve caused to millions of people.
This is why language is important — it is the way we communicate our intentions to the world.
As for the comments about legal jeopardy, CrowdStrike expressing remorse and taking some responsibility for what happened won’t make a whole lot of difference in their legal situation. It’s clear that they caused this and somebody there screwed up; that is not in dispute. Any legal justification for their failure to be remorseful is just an excuse.
I’d recommend Melissa Agnes’ book “Crisis Ready” to any company that could ever be in a situation such as this. It recommends developing a plan on what to do and how to communicate when disaster strikes. Clearly, nobody at CrowdStrike had such a plan. That’s why they look like arrogant asses right now. Making a mistake like this is unforgivable. Failing to communicate — actively — what happened and why makes it worse.
Here’s another language problem: The great Alan Cooper is fond of saying that in every other industry we talk about product defects. In the software industry we talk about bugs, putting a happy face on the fact that these problems are also product defects. In this case, CrowdStrike shipped a defective update that broke their product.
Here’s the announcement from them that I want to see: “Today we downloaded a defective update to your systems that broke your systems and shut down your business. We’re sorry that our failure to adequately perform integration testing and other standard, well-known quality control procedures cost your company millions of dollars in damages and caused your customers grief. We’re going to fire our incompetent employees who failed to do their jobs adequately, replace them with competent employees, audit our processes, fix them, and make sure that in the future we do the job you pay us to do.”